The Plan
- IAM Landscape
- Demonstrate IAM end to end
- Review components of Architecture - SMS, IDE, UDI, Directory, Identity Services
- Questions, Help, Comments?
The IAM Landscape
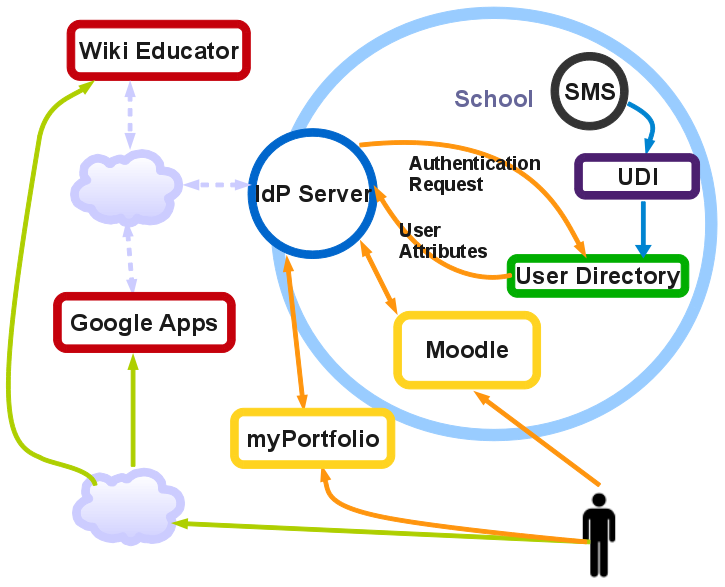
Start with the SMS
- Most reliable source of User data
- Start of the flow - new enrolments, amendments, unenrolments
- Exports available:
- KAMAR
- PC Schools
- eTAP
- MUSAC
- But more importantly - anything that can produce a CSV file
IDE data
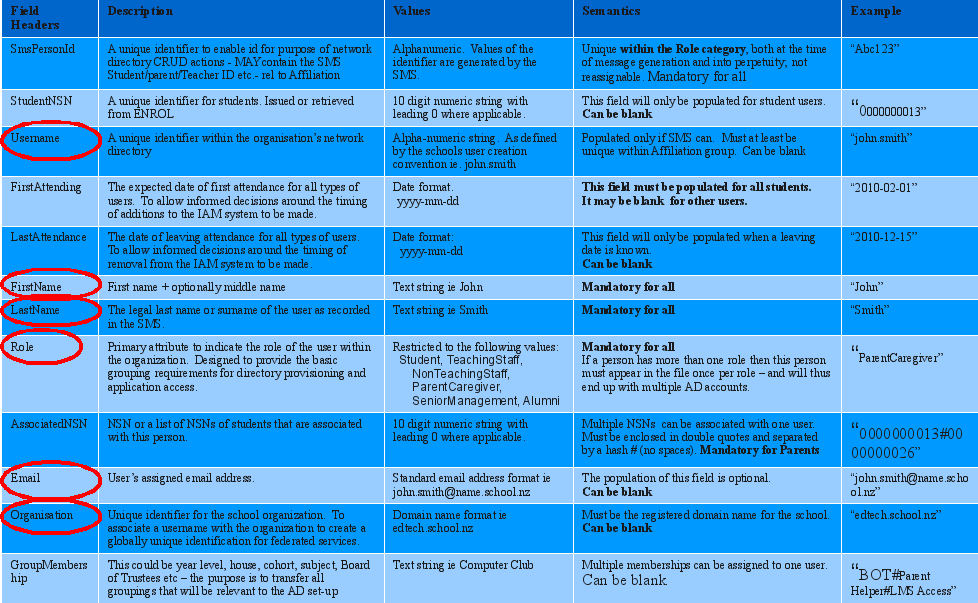
IDE data - in CSV format
"mlepSmsPersonId","mlepStudentNSN","mlepUsername","mlepFirstAttending","mlepLastAttendance","mlepFirstName","mlepLastName","mlepRole","mlepAssociatedNSN",
"mlepEmail","mlepOrganisation","mlepGroupMembership"
"SMS01",9876543210,"piers","2010-02-08","2010-12-18","Piers","Harding","NonTeachingStaff"," ","piers@hogwarts.school.nz","hogwarts.school.nz","Staff"
"SMS02",9876543211,"daffy","2010-02-08","2010-12-18","Daffy","Duck","Student"," ","daffy@hogwarts.school.nz","hogwarts.school.nz","Students#LMS Access"
"SMS03",9876543212,"","2010-02-08","2010-12-18","Daisy Elorous","Duck","ParentCaregiver","0000000013#0000000026#9876543211",
"daisy@example.com","hogwarts.school.nz","Parent#Board of Trustees"
"SMS04",9876543213,"prabbit","2010-02-08","2010-12-18","Peter","Rabbit","Student"," ","prabbit@hogwarts.school.nz","hogwarts.school.nz","Students#LMS Access"
"SMS05",9876543214,"gemima","2010-02-08","2010-12-18","Gemima","Puddle-Duck","Student"," ","gemima@hogwarts.school.nz","hogwarts.school.nz","Students#LMS Access"
"SMS06",9876543215,"curly","2010-02-08","2010-12-18","Curly","Somebody","Student"," ","curly@hogwarts.school.nz","hogwarts.school.nz","Students#LMS Access"
"SMS07",9876543216,"mo","2010-02-08","2010-12-18","Mo","Somebody-Else","TeachingStaff"," ","mo@hogwarts.school.nz","hogwarts.school.nz","Staff","Somebody-Else"
"SMS08",9876543217,"humpty","2010-02-08","2010-12-18","Humpty","Dumpty","Student"," ","humpty@hogwarts.school.nz","hogwarts.school.nz","Students#LMS Access"
"SMS09",9876543218,"dumpty","2010-02-08","2010-12-18","Dumpty","Humpty","Student"," ","dumpty@hogwarts.school.nz","hogwarts.school.nz","Students#LMS Access"
"SMS10",9876543219,"sid","2010-02-08","2010-12-18","Sid","Sloth","TeachingStaff","SMS02","sid@hogwarts.school.nz","hogwarts.school.nz","Staff#Teachers"
UDI
- based on phpldapadmin
- A mapping and Automation tool
- Can be run as a centralised service - can be configured for multiple schools/sources
- Take any CSV file, with minimum data requirement and load
- Map input attributes to one or more target attributes
- Map users by mlepRole, mlepGroupMembership 'tags' to different directory tree nodes/containers
- use mlepRole and mlepGroupMembership 'tags' to map users to Directory group membership
User Directories
- Any RFC 2251 compliant Direcory should work - eg:
- OpenLDAP
- Active Directory (not compliant but made to work anyway)
- Novell eDir
- OS-X Directory Services
What's needed in the Directory
- a new set of attributes
- attributes bundled in new Auxilliary class -> mlepPerson
- similarities with eduPerson, and other objectClasses such as inetOrgPerson, user, etc.
The Inner workings of the UDI
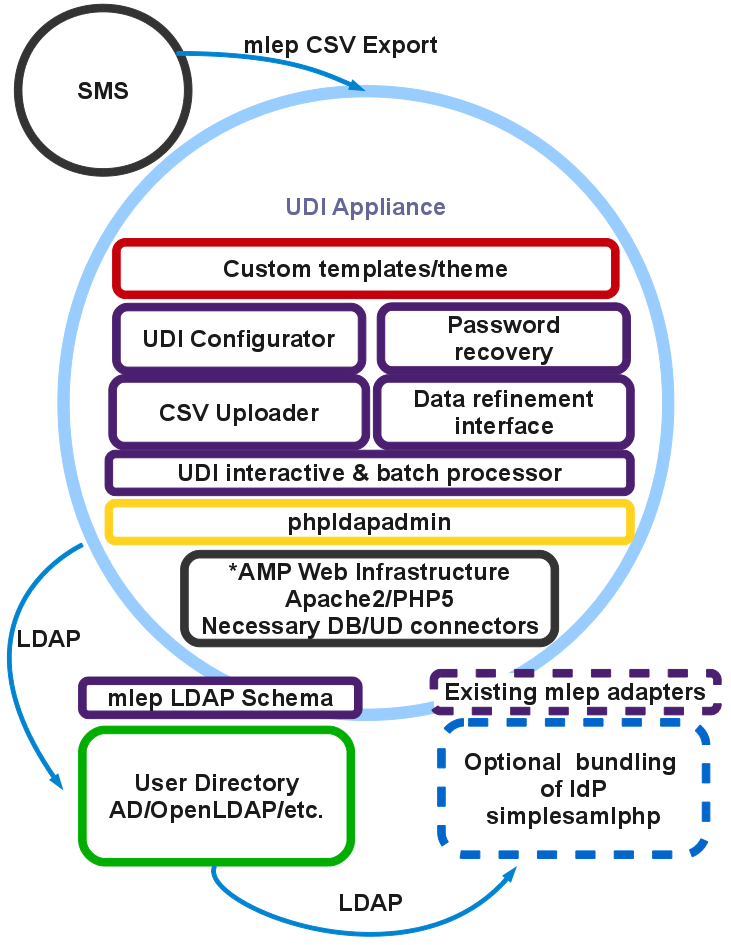
UDI - features
- generate user Ids and passwords
- Interactive processing via browser, and command line interface for scheduling
- logs and email reports
UDI - is extensible
- simple framework for writing hooks to modify all aspects of user data, or to execute follow on events:
- account_create before/after,account_update before/after, account_delete_after
- account_deactivate_after, account_reactivate_after
- passwd_algorithm
- many others from phpldapadmin
UDI - as a project
- Designed to enable contribution by:
- patches - it's OpenSource, and hosted at github, gitorious, launchpad
- plugins - come up with a feature that others will use, and it will go in
- packaging - VPS, or PHP archive (automatically packaged by github, and gitorious)
Authentication Scenarios
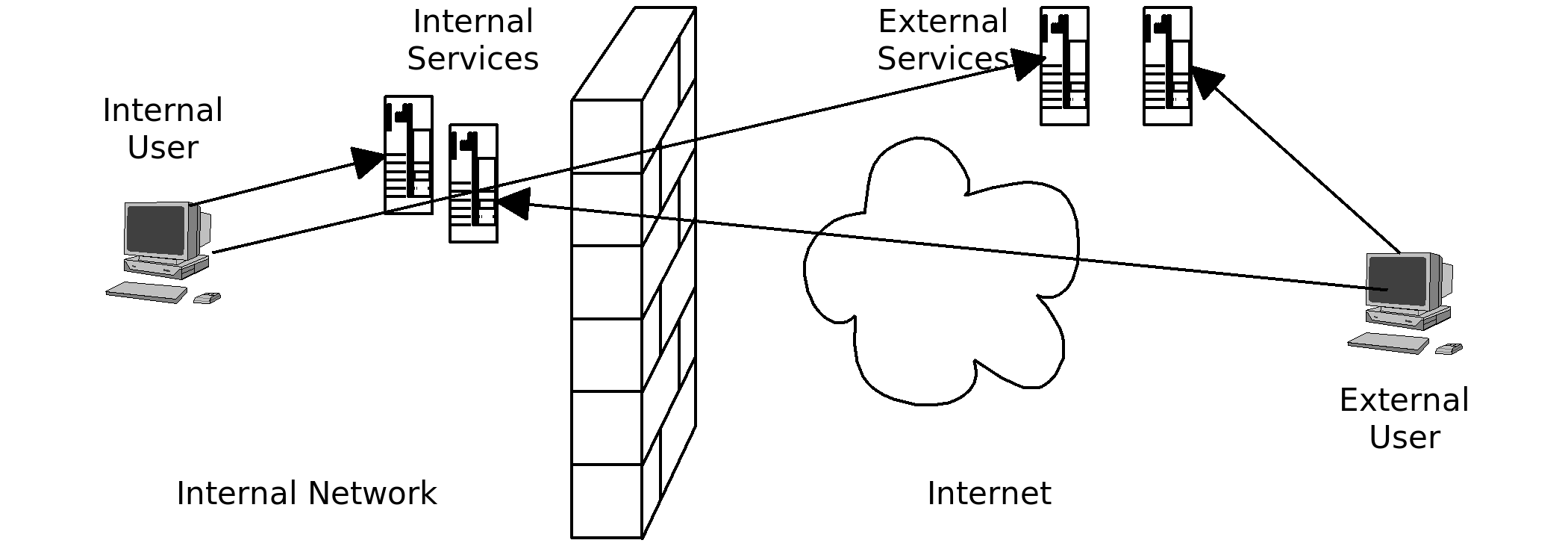
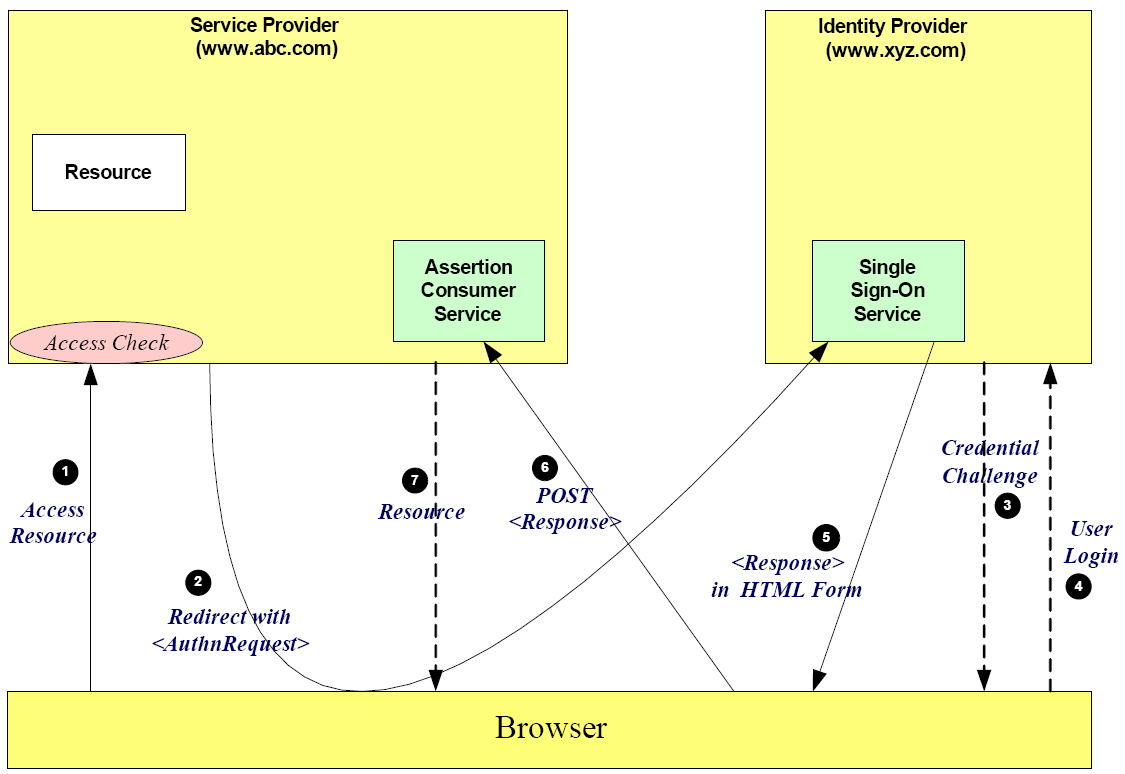
SSO - How does it work
- It is Web SSO
- It is based on SAML 2.0
- It requires a centrally stored session, that each service refers back to (passed by cookie)
Web SSO
- Not just shared credentials – Sign On once, and be automatically signed on everywhere as required.
- Sharing the necessary user attributes from a central repository.
- Is a standard formula for using browser interaction to establish a users identity (and assertions about that identity) and then to propagate this amongst subsequently accessed services.
SAML 2.0 - what is it
- It is an XML based framework for the description, and secure exchange of assertions for the proof of identity, and attributes attached to that identity
- Compenting standards are Shibboleth (compatible), OpenId (too loose)
SAML 2.0
IdP
- a colleciton of web services - login system, and SOAP responders for SAML queries
- IdP brokers the authentication and assertions about users, based on data from Directory
- Can be run by anyone - schools, loops, service providers, Government
- Reference implementations are available and OpenSource
The IdP
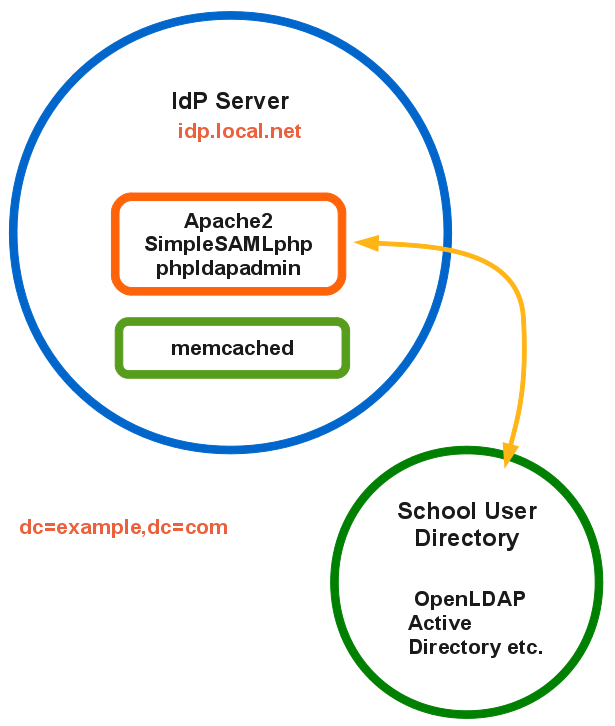
IdP - things to be careful of
- Need uniform data - not just attribute names but meanings too
- data validation within the IdP - check data complete from directory - good for multi-tenanted setups
- must add access restrictions for connections from IdP to services - especially based on mlepOrganisation
- Defacto standards - EPPN, mlepGlobalUserId, mlepUsername+'@'+mlepOrganisation
Connected Services
- So far - Moodle, MyPortfolio (Mahara), Ultranet, AccessIt, eCast, WikiEducator, Google Apps
- A growing list at http://groups.google.com/group/mle-reference-group/web/school-apps-supporting-single-sign-on
- Live @ Edu should be coming - but don't hold your breath
HowTo Connect Services
- Each service requires exchange of metadata with the IdP
- Some services eg: myPortfolio - require organisation level configuration
- Most services have user provisioning considerations
- Consider how users interact - deep URIs, Email triggers etc.
More Services - well how about bridging
- Bridge authentication protocols
- Shibboleth - eCast
- OpenId - statusnet, Pligg
- AuthMemcookie - Koha
Bridging Identity networks
- OpenId - use Google?
- Must augment user attributes as these providers don't have enough
